FAQ
WHOIS Email DCV Deprecation
Recent vulnerabilities in the domain name WHOIS system have highlighted the WHOIS-based domain-validation method as a weakness in the process of validating publicly-trusted digital certificates.
A ballot is expected to pass in the CA/Browser Forum (CABF) requiring that WHOIS-listed email addresses are no longer acceptable for domain validation, nor can historic domain validations based on WHOIS email addresses be reused.
As a result, Sectigo and all other public Certificate Authorities will be required to:
- No longer allow WHOIS-based email addresses for domain validation.
- No longer allow certificates to be issued based on a WHOIS email address validation. Domains must be re-validated using an accepted, non-WHOIS method.
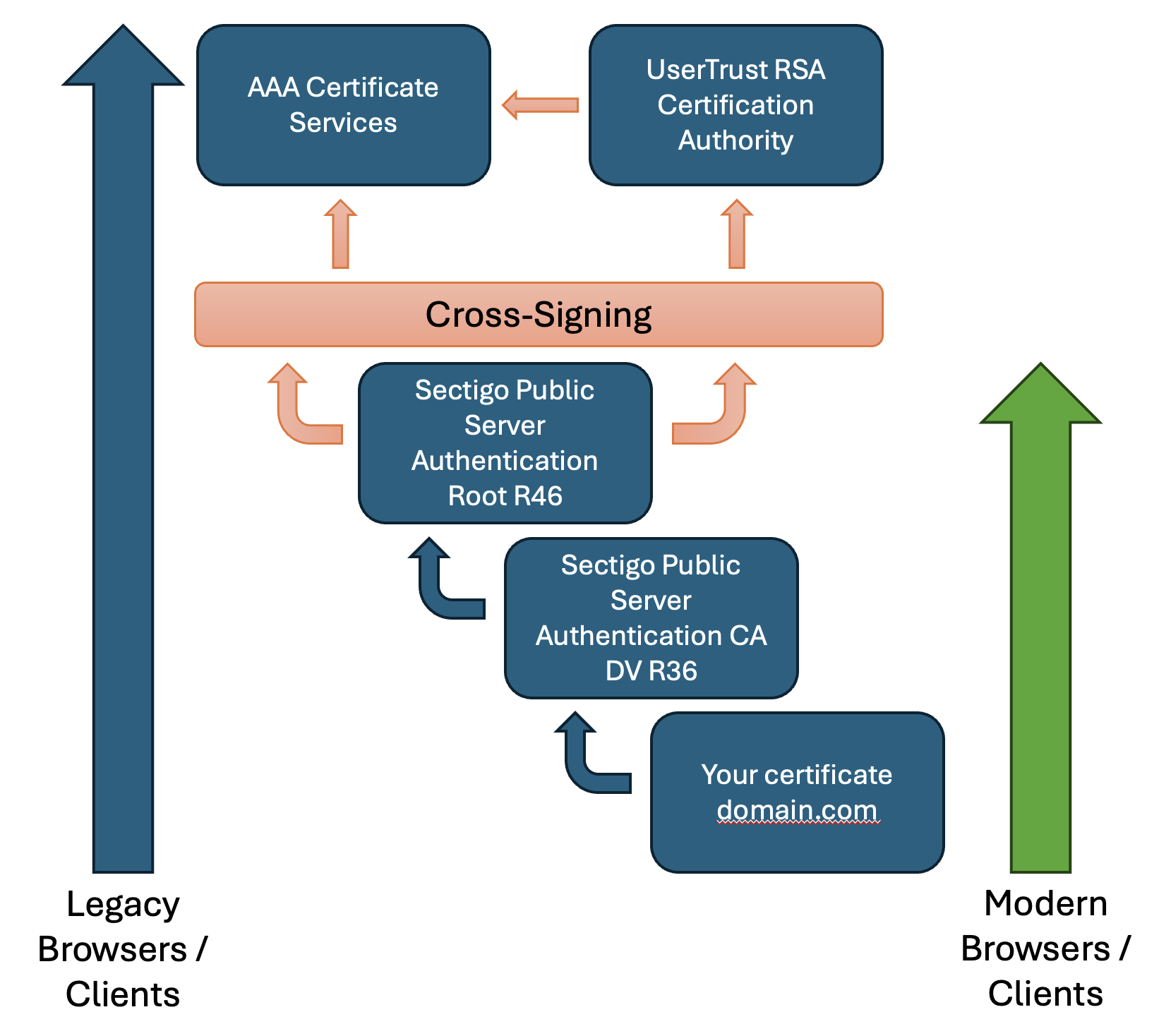
Sectigo Root CA Change - May 15, 2025
Published on and maintained in Cascade.